Latest Update (July 3rd, 2025 – 4:09AM – GMT+1): YouTuber Soufyane El Kabouri (Hikayah) has posted a video about this. You can show him support through here. He’s earned it.
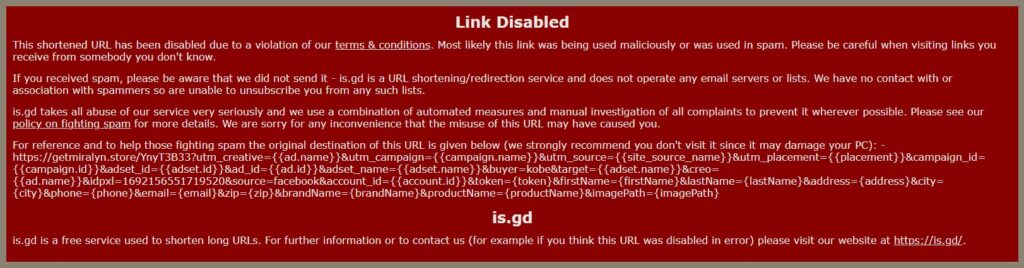
Update (June 19th, 2025 – 11:36PM – GMT+1): Looks like the is.gd short link has been disabled. Hooray! Good job, is.gd Abuse Team! Sadly, because Facebook moderation is lazy/incompetent, my buddy Sami and I will keep monitoring that post for any new malicious short links, and report them to their respective URL shortening service provider. Here’s what visiting https://is.gd/offrir_ma looks like now:
Update (June 19th, 2025 – 3:37PM – GMT+1): The fact that is.gd warns users as soon as the malicious short link gets reported is actually an amazing strategy! Moroccan Facebook users will be less hesitant to click the link now, but honestly, I’d rather is.gd takes down the short link completely, because when it comes to online shopping and impulse control, it’s better to be safe than sorry.
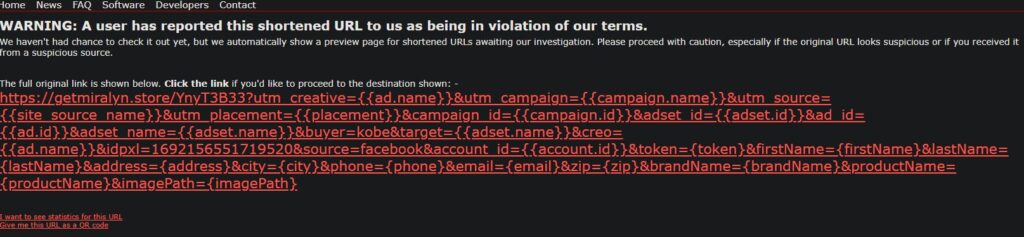
Update (June 19th, 2025 – 3:26PM – GMT+1): Scammers realized TinyURL isn’t “reliable” for them anymore to scam people, so they’re now using https://is.gd/offrir_ma I’ve already reported the new malicious short link. Let’s hope is.gd has a decent or better response time.
Update (June 19th, 2025 – 12:17AM – GMT+1): https://tinyurl.com/offrir-v15-ma has been terminated! I will keep monitoring that Facebook post for any new malicious activity. Sadly, Facebook isn’t blocking the post because of that sweet, sweet advertiser money. According to my buddy Sami, the first time his mom saw that post was on the news feed, and apparently, it was a sponsored post. That’s malvertising for ya.
Update (June 18th, 2025 – 3:48AM – GMT+1): The scammers have updated the TinyURL again: https://tinyurl.com/offrir-v15-ma; I’ve let TinyURL know about it, and I hope they terminate it asap to prevent any new victims from getting scammed.
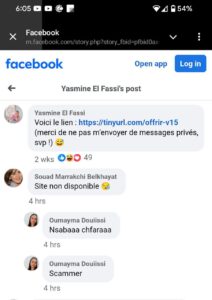
Update (June 10th, 2025 – 5:22PM – GMT+1): https://tinyurl.com/offrir-v15 has been terminated by TinyURL! It’s nice to know that they’re getting more proactive. Also, some Facebook users do leave comments pointing out that it’s a scam, but the fake FB page actively deletes those comments. See the screenshot below:
Update: The Facebook post is still up. Zuckerberg only cares about kissing Trump’s ass and the Metaverse, so his blatant incompetence is to be expected. Oh, and because the Facebook post is still up, they’re now using a different TinyURL short link: https://tinyurl.com/offrir-v15
Update: Good news, everyone! The TinyURL short link has finally been terminated. About damn time!
Due to a lack of action from domain registrars and antivirus vendors, I’m documenting this publicly to raise awareness and protect Moroccan internet users. This post outlines a deceptive phishing campaign that has targeted Facebook users in Morocco under the guise of a Dyson V15 giveaway.
Overview of the Scam
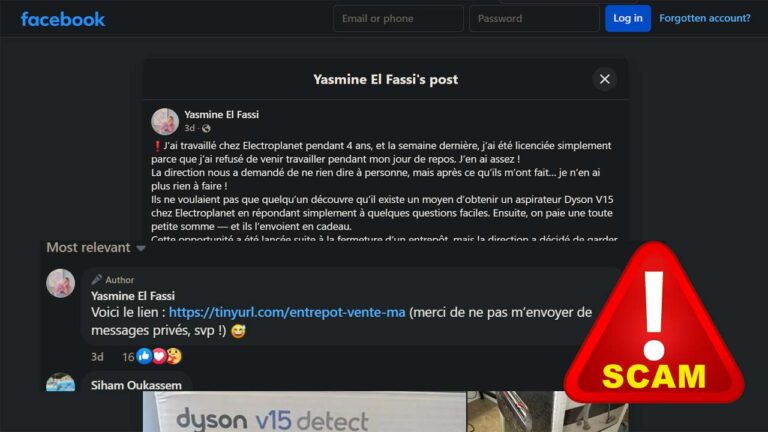
This campaign begins with a malicious TinyURL link shared in the comments of a Facebook post by a fake profile named Yasmine El Fassi. When clicked from outside Morocco, the link redirects users to a harmless article. However, Moroccan users are redirected to a fraudulent product page offering a free Dyson V15 Detect vacuum.
Victims are asked to complete a short survey. Each step leads to a different redirect, and the URLs grow increasingly complex until the user lands on a fake payment page. Once personal and credit card information is entered, the page returns an error and claims the user will receive a phone call.
Targeting Methodology
- Uses geo-targeting to serve malicious content only to Moroccan users.
- Initial link: https://tinyurl.com/entrepot-vente-ma (Reporting [email protected] did help after like a week.)
- Facebook post URL: View post (Facebook Support relies heavily on AI for moderation, so it’s pretty much useless in taking down actual harmful content.)
- Final destination: fraudulent payment pages designed to steal credit card data, and potentially double-charge unsuspecting customers.
Confirmed Malicious Domains
- plenorhq.site (Doesn’t point to a server anymore. DNS_PROBE_POSSIBLE error.)
- all4discount.world (uses CloudFlare DNS + Development mode, and shows a 404 error.)
- gostyle4life.com (was repurposed to look like a less suspicious E-Commerce site for women clothing)
- findall4cheap.xyz (Doesn’t point to a server anymore. DNS_PROBE_POSSIBLE error.)
- getsupersell.world (uses CloudFlare DNS + Development mode, and shows a 404 error.)
- blakfridaysales.click (Ditto)
- specialboxprizeclothing.click (Ditto)
- frst-sw.com (blank page)
- specialboxprizeclothing.click (uses Cloudflare DNS, and shows a 404 error)
- cashrushapp.sbs (Ditto)
- hifisoundclub.com (was repurposed to look like a less suspicious E-Commerce site for electronics)
- glowskingo.com (was repurposed to look like a less suspicious E-Commerce site for women skincare products)
- gleamtone.com (Ditto)
- promoblaster.sbs (uses CloudFlare DNS + Development mode, and shows a 404 error.)
- myfavecar.com (was repurposed to look like a less suspicious E-Commerce site for car products and kids’ bicycles and equipment)
- getgliso.store (when visited with a particular query string from the the TinyURL above, it redirects Moroccan users to a fake Dyson v15 product page.)
- ijusthobby.com (when visited with a particular query string, and a non-desktop user-agent (e.g., iPad iOS 13.2) it doesn’t throw the usual error 500, but instead, it redirects to the checkout page, so if a victim enters their credentials there, then it’s over, and every time the checkout page URL changes, the payment processor credentials change as well, so each fraudulent transaction will have a different vendor.
- getmiralyn.store (same crappy behavior (fake survey/product page, etc, etc. Scammers are known to be lazy unoriginal script kiddies with Peter Pan Syndrome.)
- cheap-world-deals.xyz (This domain is used to host the fake checkout page. Each new victim is redirected to a long URL, mind you.)
- joytoypro.com (This domain is used to host the fake secure payment page. Each new victim is redirected to a long URL, mind you.)
Each of these domains uses services such as Cloudflare for DNS and is hosted under registrars known for low-cost or unregulated domain registrations. You should NEVER try to buy anything from these sites under any circumstances!
Registrar Abuse Contacts
| Domain | Registrar Abuse Contact |
|---|---|
| gostyle4life.com | [email protected] |
| all4discount.world | [email protected] |
| plenorhq.site | [email protected] |
| findall4cheap.xyz | [email protected] |
| easytosellamerica.lat | [email protected] |
| getsupersell.world | [email protected] |
| blakfridaysales.click | [email protected] |
| specialboxprizeclothing.click | [email protected] |
| frst-sw.com | [email protected] |
| cashrushapp.sbs | [email protected] |
| hifisoundclub.com | [email protected] |
| specialboxprizeclothing.click | [email protected] |
| glowskingo.com | [email protected] |
| gleamtone.com | [email protected] |
| promoblaster.sbs | [email protected] |
| myfavecar.com | [email protected] |
| getgliso.store | [email protected] |
| ijusthobby.com | [email protected] |
| ijusthobby.com | [email protected] |
| getmiralyn.store | [email protected] |
| joytoypro.com | [email protected] |
Case Study: A Victim’s Experience
A friend’s mother fell victim to this scam after seeing the Facebook post. She entered her credit card information and was charged twice. As of the time of this writing, she is contacting her bank to try to recover the funds.
UPDATE: Sadly, the bank told her there was nothing to be done. What’s crazy is that the scam happened on Saturday, and she went to the bank on Monday, so I can’t help but feel like the bank is just being lazy/incompetent.
Security Observations
- Random fake data causes server errors, but realistic fake data occasionally allows the scam to proceed.
- Payment pages accept sensitive information without validation.
- Each visit and submission leads to different domains and increasingly obfuscated URLs.
Recommendations
- Do not trust giveaway claims on social media, especially those using link shorteners.
- Educate family members and especially older users on common phishing tactics.
- Use browser tools or VPNs to inspect geo-based redirects.
- Report malicious URLs and behavior to hosting providers, DNS services (like Cloudflare), and abuse contacts.
- If you’ve submitted personal or payment data, contact your bank immediately and monitor for suspicious activity.
Conclusion
Despite reporting the above domains to registrars and security vendors, many remain live or are quickly replaced by alternate versions. I’m publishing this in the hope that transparency and public documentation will help curb the spread of such campaigns.
If you are a registrar or a DNS provider reading this, consider this a call to action to review your abuse handling processes. Inaction only emboldens threat actors who are now comfortably targeting entire demographics.
For screenshots and more details, please check this PDF: Scam_Report_involving_4_domains_registered_with_3_different_registrars; I kept trying to send this PDF to the 3 registrars, so that they can do something about the malicious domains, but my emails kept getting rejected by their systems no matter how many times I tried to send them the evidence they asked for.